Published
Last 1 week
Last 30 days
Latest 24 hours
Profession
Published
Profession
Industry
Seniority
64
jobs
HR-EX Consulting
Lagos, Nigeria
HR-EX Consulting
Lagos, Nigeria
Hilton Hotels & Resorts
Abuja, Nigeria
Marriott International
Akwa ibom, Nigeria
Marriott International
Lagos, Nigeria
Marriott International
Lagos, Nigeria
Eat 'N' Go Limited
Lagos, Nigeria
Bukka Hut
Lagos, Nigeria
Bukka Hut
Lagos, Nigeria
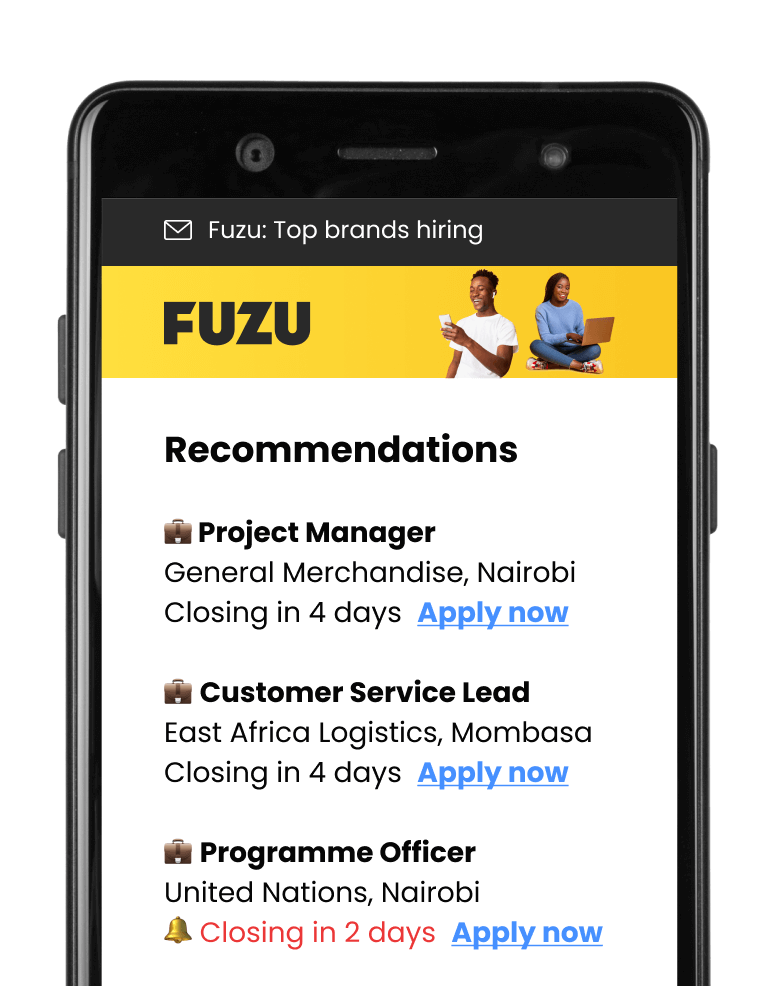
Get personalised job alerts directly to your inbox!
Bukka Hut
Lagos, Nigeria
Closing: May 23, 2024
6 days remainingPublished: May 8, 2024 (9 days ago)
Education:
Work experience:
Language skills:
Contract Type:
Sign up to view job details.
Education, Experience & Skills Required
Education, Experience & Skills Required

Applications submitted via Fuzu have 32% higher chance of getting shortlisted.